This section presents instructions for enabling secure connections to Ansys License Management Center (LM Center), using a Tomcat web server.
When communications between the client browser and the front-end web server need to travel over an untrusted network such as the Internet, it is highly advisable to use secure connections between the client browser and the front-end web server. SSL, or Secure Socket Layer, is a technology which allows web browsers and web servers to communicate over a secured connection. Data is encrypted by each communicator, transmitted and then decrypted by the other communicator. Additionally, the SSL protocol authenticates credentials during your initial attempt to communicate over the secure connection.
When implementing SSL, a web server must have an associated Certificate for each external interface (IP address) that accepts secure connections. This provides a level of identity assurance during communication. The certificate is cryptographically signed by its owner, and is therefore extremely difficult for anyone else to forge.
SSL/TLS certificates are typically purchased from well-known Certificate Authorities (CA) such as VeriSign and Thawte. Using a certificate from a well-established and widely recognized CA confers several benefits to the web server operator. These include increased credibility and convenience because the root certificates for popular CAs are prepackaged into major browsers, eliminating the need to distribute anything to client browsers that will connect to the web site.
If a web server is to be used solely internally within an organization, then the benefits of using a certificate from a well-recognized Certificate Authority may not be important. Any valid SSL/TLS certificate can be used to encrypt traffic between client browser and web server as long as the client browser accepts the certificate. For internal production use, and certainly for test use, it is often sufficient to create and use an in-house Certificate Authority that can sign SSL/TLS certificates for these use cases.
A certificate that is signed by the same party that created it is known as a self-signed certificate. When an internally-generated certificate is signed using an in-house Certificate Authority, then a self-signed certificate is created. Self-signed certificates are perfectly usable for enabling HTTPS connections to a web server. However, when a browser encounters a certificate that has been signed by an unknown certificate authority, it will present the user with a warning, such as the following:
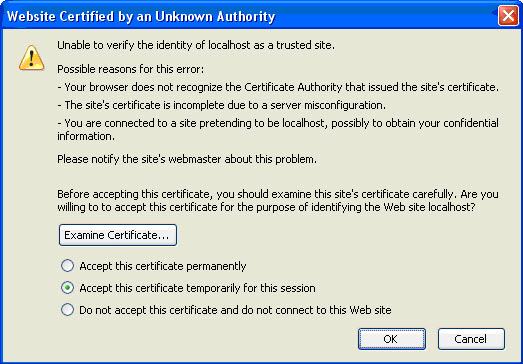
Once a user accepts the certificate, the HTTPS connection can proceed.
In cases where authenticity may be less of a concern but privacy is necessary, Java provides a relatively simple command line tool called "keytool". Keytool can create a simple, user-generated "self-signed" certificate. The following instructions describe how to configure keytool and Tomcat for SSL. We recommend that you read the Preparing the Certificate Keystore and Editing the Tomcat Configuration File before beginning the configuration.
Tomcat currently operates only on JKS, PKCS11 or PKCS12 format keystores. The JKS format is Java's standard "Java KeyStore" format, and is the format created by the keytool command-line utility. This tool is included in the JDK and is what can be set-up using Ansys supplied tools. The PKCS12 format is an internet standard, and can be manipulated via (among other things) OpenSSL and Microsoft's Key-Manager.
Using the keytool command line, create the keystore file as follows:
Go to the tools directory in your installation and execute the following platform specific commands:
Windows
cd "C:\Program Files\ANSYS Inc\Shared
Files\licensing\tools"
Run the following command to create the file tomcat\conf\keystore:
java\winx64\bin\keytool.exe -genkey -alias tomcat -keyalg RSA -keystore
tomcat\conf\keystore
Linux
cd /ansys_inc/shared_files/licensing/tools
Run the following command to create the file /licensing/tools/tomcat/conf/keystore:
java/linx64/bin/keytool -genkey -alias tomcat -keyalg RSA -keystore
tomcat/conf/keystore
Tomcat can use two different implementations of SSL:
JSSE implementation provided as part of the Java runtime (since 1.4)
APR implementation, which uses the OpenSSL engine by default
The JSSE implementation can be set-up using Ansys supplied tools.
To configure the server.xml file using JSSE do the following:
Go to the licensing/tools/tomcat/conf directory in your installation and edit the server.xml file by adding:
<Connector protocol="org.apache.coyote.http11.Http11NioProtocol"
port="8443" maxThreads="150"
scheme="https" secure="true" SSLEnabled="true"
keystoreFile="conf/keystore"
keystorePass="changeit"
keyPass="changeit"
clientAuth="false" sslProtocol="TLS" />where "changeit" is the password you specified when you created the keystore file above.
You can now use Ansys License Management Center with HTTPS by restarting your Ansys Licensing Tomcat service and pointing to https://localhost:8443/ANSYSLMCenter.html.
To use the HTTPS secure connection exclusively:
Open the server.xml file in the licensing/tools/tomcat/conf directory
Remove or comment out the following 1084 connector entry:
<Connector port="1084" protocol="HTTP/1.1"
connectionTimeout="20000"
compression="on"
address="127.0.0.1"
compressionMinSize="2048"
noCompressionUserAgents="gozilla, traviata"
compressableMimeType="text/html,text/xml"
redirectPort="8443" />


