Specifying Azure Subscription Information
When a tenant administrator successfully sets up Ansys Access on Microsoft Azure, the associated Azure subscription is displayed on the Azure subscriptions page in Ansys Access on Microsoft Azure (see Azure Subscriptions).
If you want to use a different Azure subscription with Ansys Access on Microsoft Azure, follow the steps below.
-
On the main toolbar, click
 to display the Administration menu.
to display the Administration menu.
- In the navigation pane, select Azure subscriptions.
-
On the Azure Subscriptions page, click Add
subscription.
Note: If there is an existing subscription listed, you must remove it before adding a new one. Multiple subscriptions are not supported.
-
On the Add an Azure subscription page, specify the following
information:
Azure subscription ID. The 36-character Subscription ID as it appears in the Azure portal.
Resource group name. The name of the resource group associated with the Azure subscription.
Account nickname. A meaningful name to identify the subscription in Ansys Access on Microsoft Azure.
-
Click Add Azure subscription. The subscription is added to the
Azure Subscriptions list.
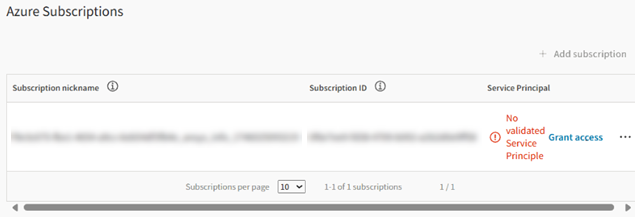
You must grant consent for a service principal to be created inside your company's Azure Active Directory (AAD).
- In the table row, click Grant access. A guided setup is displayed.
-
Specify whether you want to allow Ansys to automatically remove its
trust relationship during offboarding.
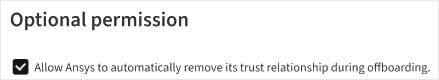
If this setting is enabled, the Application.ReadWrite.OwnedBy permission is requested for the service principal created for Ansys Access on Microsoft Azure in your company's Azure Active Directory. If you choose to offboard your tenant from Ansys Access on Microsoft Azure, this permission lets Ansys automatically delete the service principal, removing Ansys's access and trust relationship from your Azure tenant.
If this setting is disabled, you must manually remove the trust relationship after offboarding your tenant from by Ansys Access on Microsoft Azure by cleaning up Ansys-related roles and permissions in Azure.
-
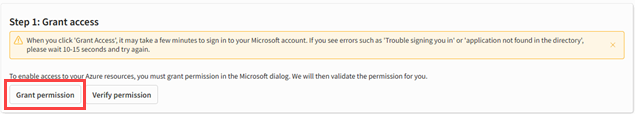
Under Step 1: Grant access, click Grant
permission.
-
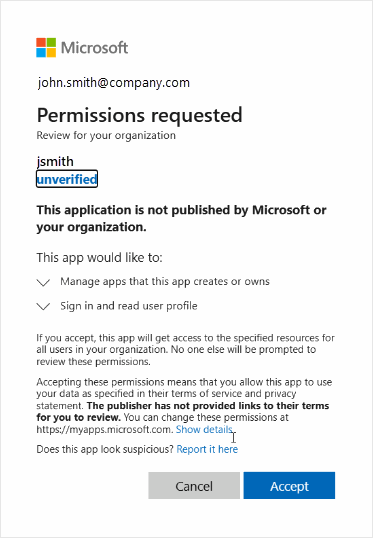
In the Microsoft dialog, select the account to be used to access your Azure tenant.

Permissions are requested:
 Note: If Allow Ansys to automatically remove its trust relationship during offboarding was disabled in the earlier part of the setup, the permission to Manage apps that this app creates or owns is not listed and will not be requested.
Note: If Allow Ansys to automatically remove its trust relationship during offboarding was disabled in the earlier part of the setup, the permission to Manage apps that this app creates or owns is not listed and will not be requested.For information about the permissions being requested, see Service Principal Created for Ansys Access on Microsoft Azure.
- Review the conditions of the permissions request, then click Accept.
-
Click Verify permission.
The account is validated:
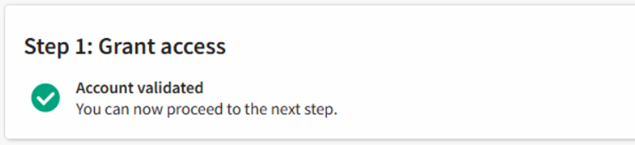
-
Deploy an Azure Resource Manager (ARM) template by following the instructions provided
in Step 2: Deploy an ARM template.
The template creates two custom IAM roles in the Azure Role-Based Access Control (RBAC) system. For information about these roles, see IAM Roles Created for Ansys Access on Microsoft Azure.
The custom roles are assigned to the service principal, enabling Ansys Access on Microsoft Azure to create and manage infrastructure on your behalf within your Azure environment. This setup ensures that the necessary permissions are in place for seamless integration and operation of Ansys Access on Microsoft Azure in Azure Active Directory.
When the ARM template has been deployed and the permissions have been validated, a confirmation message is displayed:

-
Click Submit. The subscription listing now displays a validated
service principal.
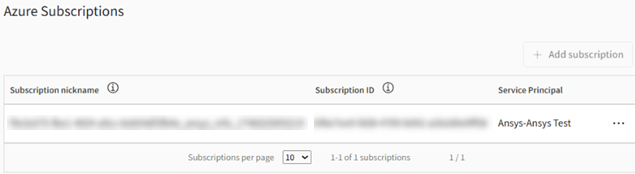
You can now add locations to the configuration.


